


Information Security
Information security includes company
policies, standards and solutions that should be incorporated in the
design of business processes and information flows to ensure access to
data is authorized. These company
Personnel SecurityThe following personnel security components exist at KHA:
Operational Security: Risk AssessmentGuiding Principle The results of a risk assessment are only the beginning of an ongoing process aimed at reducing the possibility of, or degree to which, systems will be adversely affected by a security event. KHA will continually update its assessments as components are changed, and applications replaced.
Periodic reassessments are done to maintain an accurate picture of the enterprise’s security posture. As results are reported, changes in policy are made to better address the weak points in the existing security program.
Systems’ Role in Risk Mitigation and Assessment Systems incorporate in their design the risk mitigation they decide to implement. The controls that a system selects should address specific, identified vulnerabilities, or specific identified threat-sources, thereby reducing the overall threat it faces. The beginning of the system life cycle is the best time to address security to ensure cost effective, interoperable solutions.
Systems should choose controls or security goals after evaluating risks (risk-adjusted goals. Costs affect goals and sources of costs are:
A system should adjust security controls using the following guidelines:
Physical SecurityThe following are physical security measures in place at KHA:
Network SecurityThe following are network security measures:
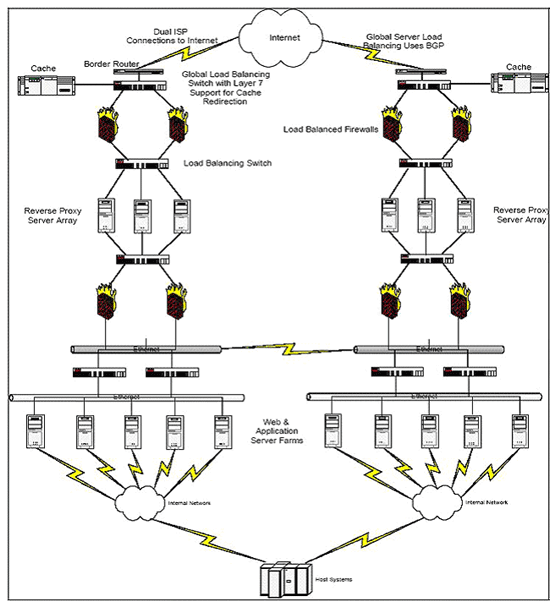
The diagram below shows KHA’s Firewall: |
|
|
|
Data packets that go in and out of the KHA will use non-SSL and SSL with a 128-bit encryption. The firewalls control access to ports 80 and 443 while the Reverse Proxy servers hide the actual IP addresses of KHA devices. |
© 2008 CMU/Boeing Class - all rights reserved